暗网术语表
Alias: A screen name intended to conceal a user’s identity, with little to no ties to the user’s actual personal information.
Bitcoin: One of the most popular cryptocurrencies in use today. As of publication date (3/24/17), 1 Bitcoin = 984.35 U.S. dollars.
Blockchain: Essentially a distributed database. Information within a blockchain is publicly shared across all participating users or machines. With regards to Bitcoin, the Bitcoin blockchain is a public record of all Bitcoin transactions which helps to verify transactions and prevent double spending.
Botnet: A network of computers, or other IoT devices, infected with malware and being used (often unknowingly by device owner(s)) to send spam or support DDoS or other attacks.
Brute Force Attack: The trial-and-error entry of passwords and/or passphrases until the correct one is guessed and entry is gained.
Carding: The practice of stealing and selling credit card information.
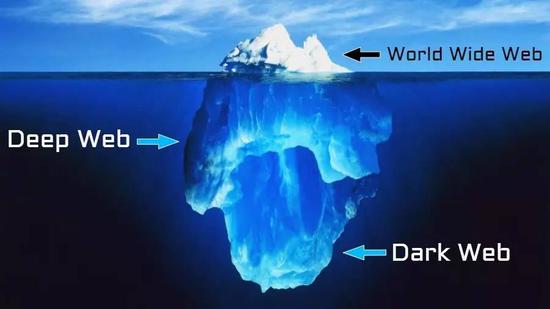
Clearnet: The “regular” internet (non-Tor), often referred to as the surface web.
Counterfeiting: The practice of forging and imitating legitimate services.
Cryptocurrency: Virtual currency that employs cryptography for security purposes.
DARKINT: Short for darknet intelligence, DARKINT encompasses actionable data from the darknet and other interconnected sources, including Tor, IRC channels, hacker forums, FTP servers, paste sites, high-risk surface internet and more.
Darknet: A network, built on top of the internet, that is purposefully hidden; it has been designed specifically for anonymity. Unlike the deep web, the darknet is only accessible with special tools and software - browsers and other protocol beyond direct links or credentials.
Darknet Footprint: A measure of your organization’s presence on the darknet. A darknet footprint looks at the volume of an organization’s digital data that could be used for nefarious purposes, exposed on the darknet as a result of hacks, breaches, or other leak(s).
Darknet Market: A marketplace website hosted on a darknet (such as Tor), setup to provide the sale of goods and services while maintaining anonymity of vendors and buyers; also known as a cryptomarket.
Dark Web: Another way of referring to the darknet.
Denial of Service (DoS): A malicious attack on a network that is executed by flooding a server with useless network traffic, exploiting the limits of TCP/IP protocols and thus rendering the network inaccessible.
Domain Name Server (DNS): The internet’s equivalent to a phonebook. On the surface web, this consists of a routing table, translating a character based domain name (ending in *.com, *.net, etc.) to the server’s IPv4 32-bit IP address. In the darknet, a special set of Tor DNS servers correlate the *.onion sites to the source, usually through a series of proxies to obscure the server’s identity.
Dox: The act of posting or publicizing an individual’s personally identifiable information (PII), commonly done to expose said individual’s true identity or for other, typically malicious, purposes.
Encryption: The process of converting data to an unrecognizable or “encrypted” form. It is commonly used to protect sensitive information, including files, storage devices, and data transfers, so that only authorized parties can view it.
Exit Scam: A scam in which a darknet market admin or vendor shuts down operation while stealing as much money as possible from their users and/or buyers in the process.
Firewall: Hardware and/or software that is specifically designed to protect a network or system from unauthorized access through employing specific rules to control and direct incoming and outgoing network traffic.
Forum: A digital environment where ideas and topics can be discussed freely among users. Members of forums generally log in with a screen name or alias to post and comment on content. Forums differ from real-time internet messaging and chat rooms in that the topics and information are not intended to be discussed real-time but instead posted for all users to see over a more extended period of time.
Grey Hat: Refers to a hacker who might utilize black hat hacking methods with an ethical, or “white hat,” intent.
Hacking: The process of identifying targeted computer information systems of interest and employing a computer program to gain unauthorized access to the target system.
Hidden Service: Another term for a .onion (Tor) site.
Honey Pot: A website or hidden service setup by law enforcement in an attempt to attract and identify individuals who participate in illegal activity.
I2P (Invisible Internet Project): An “anonymous overlay network” using the garlic routing protocol that encrypts multiple messages together to make data traffic analysis difficult, while simultaneously increasing network traffic speed. Each encrypted message has its own specific delivery instruction, and each endpoint works as a cryptographic identifier or what we refer to as “keys.” Since it’s entirely peer-to-peer in structure, there’s no hard-coded trusted set of directory stores. Instead, the network directory of I2P is netDb, a distributed database that is replicated across the network.
Internet Relay Chat (IRC): A popular text-based chat service enabling users connected to a server to communicate with each other in real-time.
IP Address (aka Internet Protocol): A unique string of numbers separated by periods that identifies a computer connected to the internet, e.g. 192.168.10.2 (iPv4).
Malware: Malicious software designed to access a system and perform unwanted actions on behalf of a third party.
Metadata: Refers to data that provides information about a certain item’s content. For example, an image may include information that describes how large the picture is or when the image was created, while a text document may contain information about the author of the document, or the IP address of the document’s author, and so on.
Mirror site: A site with the same content as another site but a different domain.
Open Source: Open source refers to any program or software that is freely available to the public. Unlike commercial software, open source programs can be modified and distributed by anyone and are often developed as a community.
OPSEC: Standing for “Operations Security,” OPSEC is a term that originated from military jargon and has since become popular with the information security industry. In general, OPSEC refers to the standards by which a person or organization should function to ensure that a security breach (of any nature) does not occur. For example, leaving the pin code to a company’s entrance key pad written on a sticky note where roaming eyes can see it might be considered negligence of company OPSEC.
Packet: A formatted unit of data routed between its origin and a destination. Data packets are used in internet protocol (IP) transmissions to navigate the internet and darknet.
Pastebin: A surface net site used to publicly post and store text for a certain, often short, period of time. Pastebin ties closely with the darknet as it is an easy way to anonymously share information without the need for a specialty based browser, such as Tor.
Payload: Data being carried or transmitted, typically the functional piece of a computer virus.
Peer-to-Peer (P2P): An ad-hoc connection of computers where information can be passed directly between the participants. In a P2P, each node of the network functions as both the server and the client.
PhaaS: A new term that refers to a phishing package that is offered in SaaS format. These packages are sold on the darknet and provide everything a novice hacker might need to run a phishing scam, including templates, tech support and tutorials.
Phishing: A data collection method used in social engineering. Phishing targets sensitive information (usernames, passwords and credit card details), often for malicious intent, by disguising itself as a trustworthy entity in an electronic communication. See spoofing below.
Protocol: Refers to the scheme in which internet content is retrieved and displayed to a browser. Tor and the darknet leverage “non-standard communication protocol” which refers to the complex set of onion proxy methods to obscure the identity of the requestor and the content server. Protocol can also refer to a method of financial transaction, e.g. bitcoin.
Relay (aka node): Within Tor there are over 7,000 relays, mostly internal. When a request to access a particular hidden service is made, the browser calculates the optimal route through a series of relays, exchanging cryptographic keys between nodes, to display the content without disclosing the IP address of the request originator.
Router: The hardware used to forward packets of information along a network, performing the traffic directing functions of the internet.
Sandbox: An isolated, controlled environment within which potentially dangerous programs are run. In a Sandbox, one can install, open and examine computer applications, potential phishing emails or infected documents without threatening the safety of the rest of the computer (or any place outside of the sandboxed environment).
Scraping: In the context of web scraping, this term describes the process of harvesting large sets of data from websites and storing the content in a database on a local computer or server.
Screen Name: The name a user employs to communicate with others online.
Social Engineering: Psychological manipulation of people into performing actions or divulging confidential information.
Spoofing: The process of falsifying the origin of network communication (via the internet) in order to mislead or misdirect the recipient. Example: A fake email from your bank asking you to validate credit card or personally identifiable information.
Tor (aka The Onion Router): A free web browser designed for anonymous internet browsing and protection against network traffic analysis; the most commonly used tool for accessing and browsing the darknet.
Tumble: A method of scrambling or anonymizing the source of one’s bitcoins.
Username: A string of characters used to log in to a computer information system.
VPN: A Virtual Private Network (VPN) is a means of re-routing a connection to the internet through privacy enhanced “tunnels,” providing the subsequent internet traffic with an added layer of security and anonymity.
Wikis: Like the surface net site Wikipedia, a darknet wiki is a website that allows registered users to collaboratively write and edit content directly from their browser. Example: The Hidden Wiki.
Zero-day: A security gap or vulnerability in a piece of software or a system that is not yet known to the software or system vendor. Once discovered, it may be exploited by attackers using a zero-day exploit.
ZeroNet: One of the newest darknets, becoming increasingly popular around the world. It’s a combination of trackerless Bittorrent and a blockchain for persistent site and user identity. It can optionally use the Tor network as a virtual private network. As a full mesh network, all clients are also servers. By browsing to a “zite” as they’re known in ZeroNet lingo, you are serving up the content you are viewing.